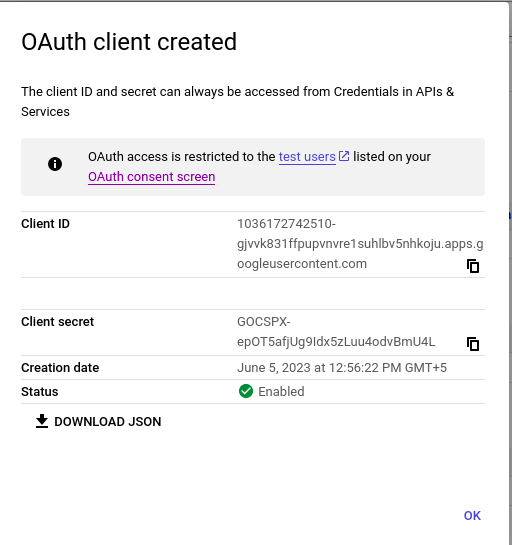
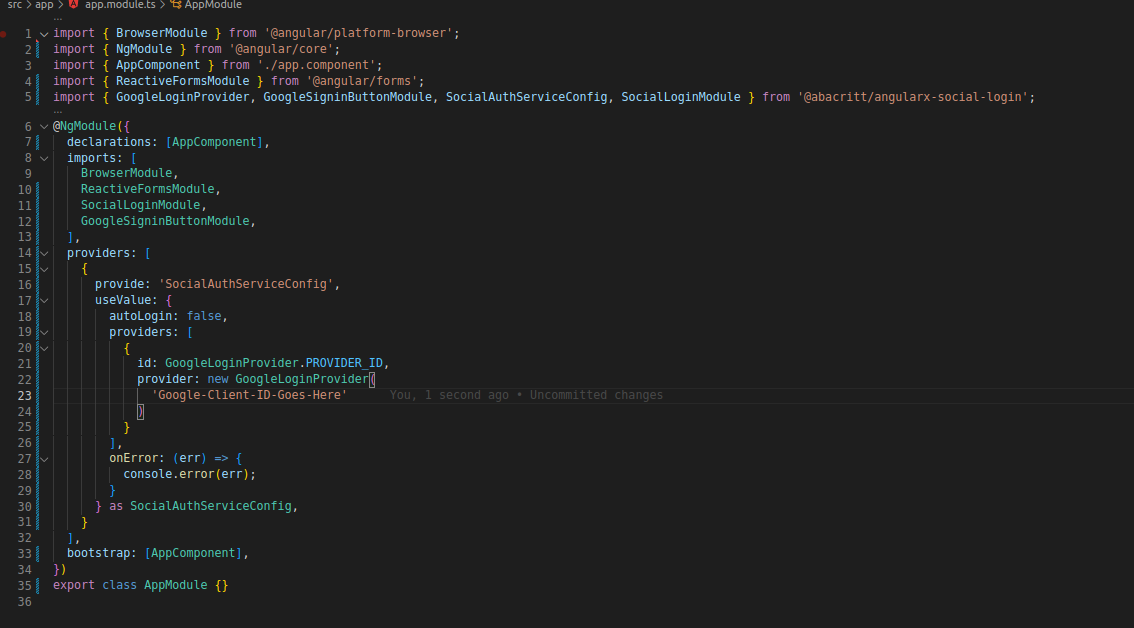
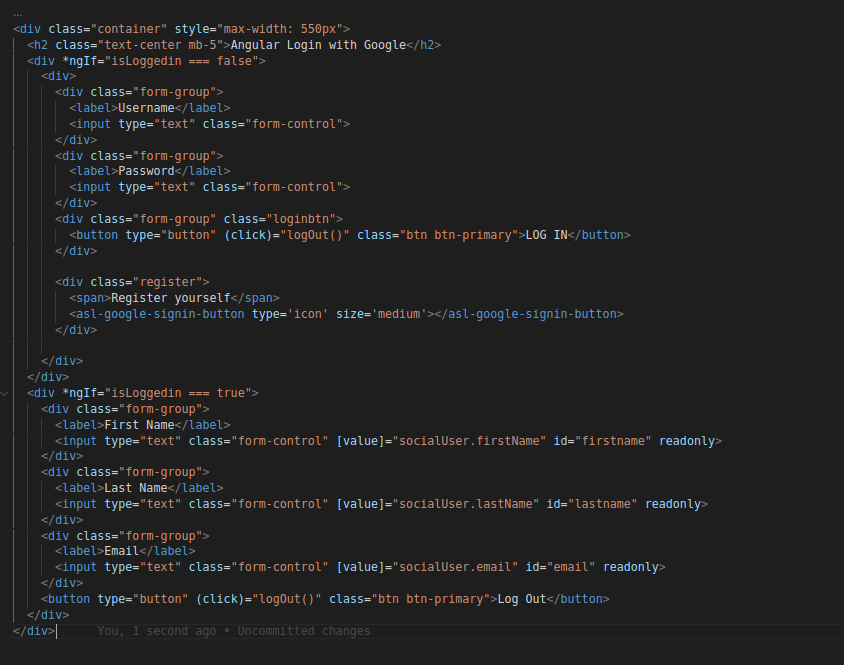
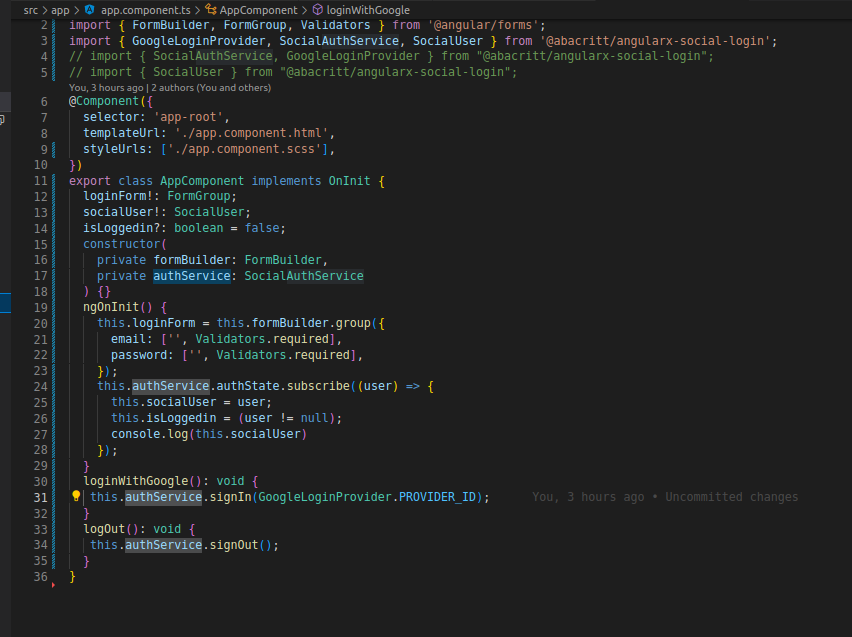
Introduction
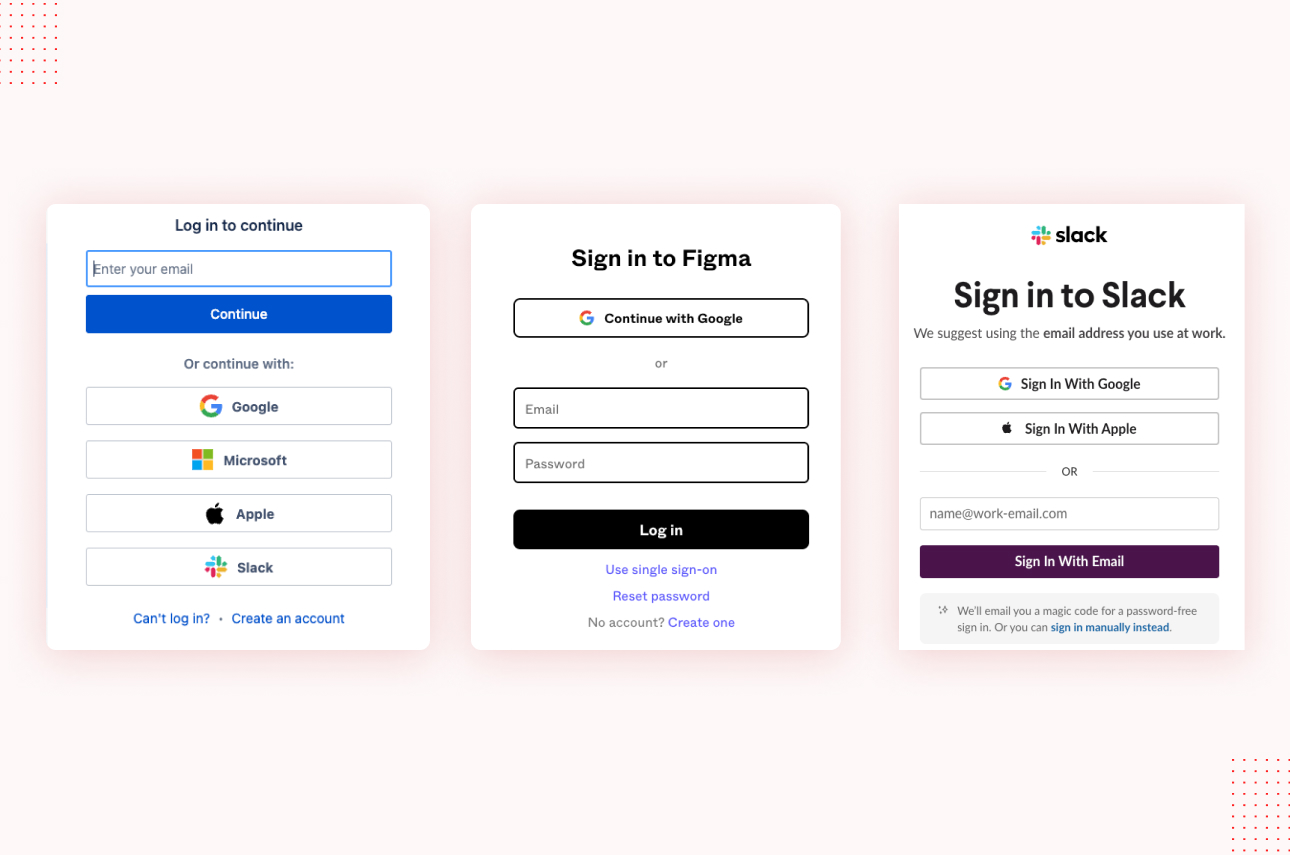
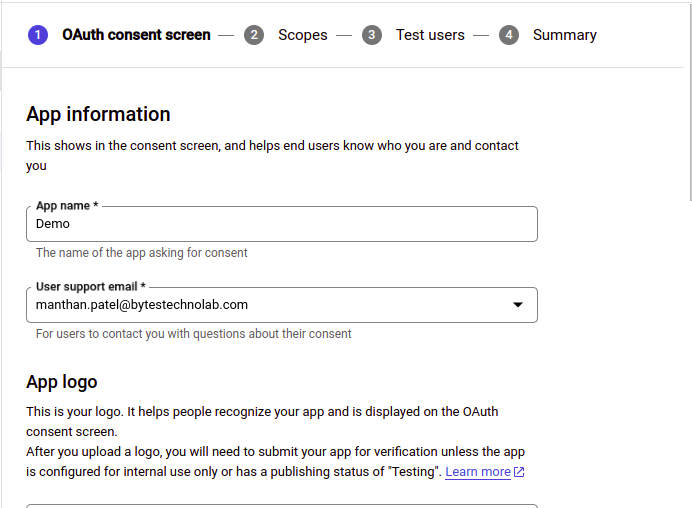
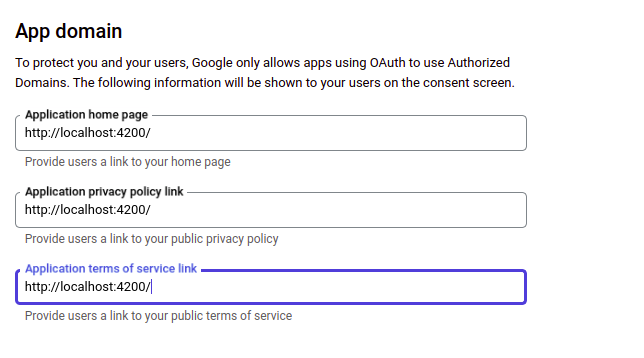
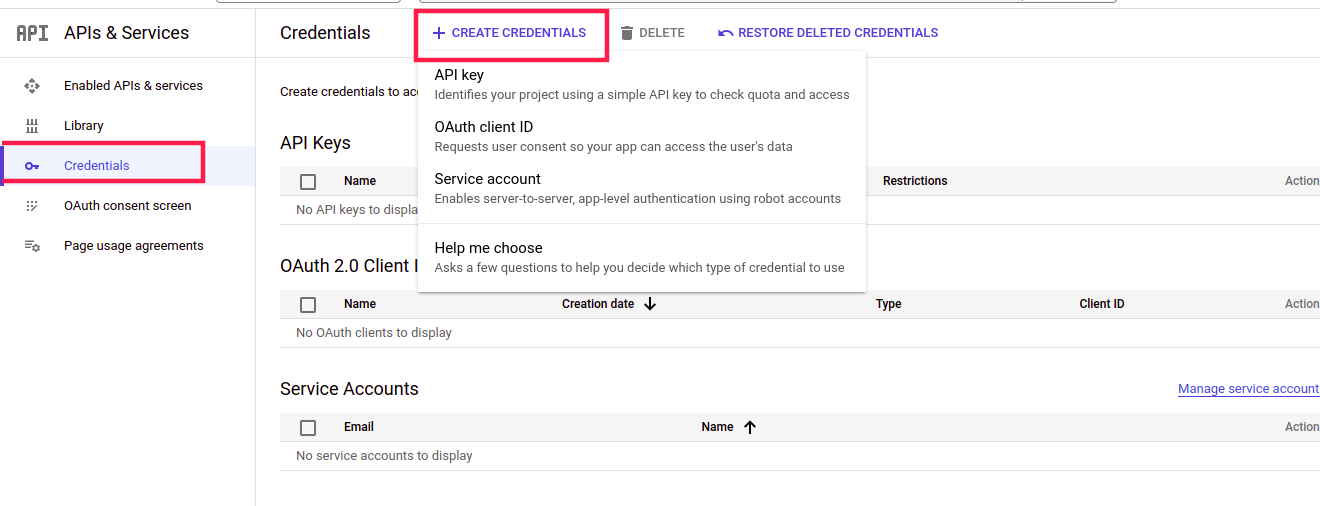
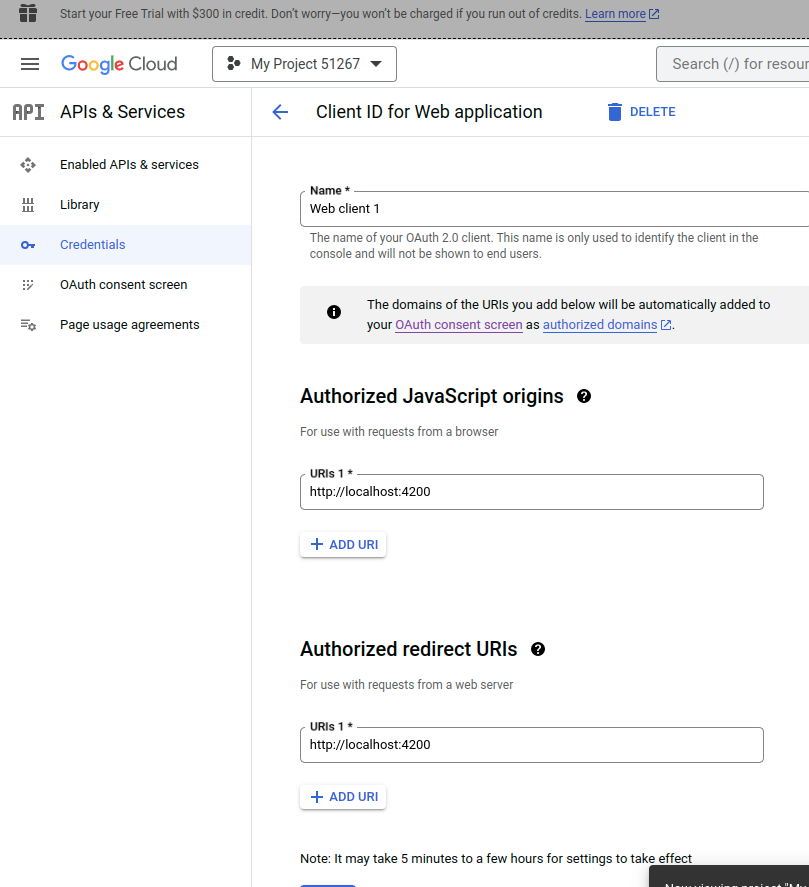
Single sign-on (SSO) is the most common and popular authentication feature in modern web applications. Instead of requiring users to remember and enter separate usernames and passwords for each application, SSO enables them to log in once and gain access to multiple resources seamlessly.
When a user attempts to access a protected resource using the login credentials, the resource requests authentication from the IDP (identity provider). The IdP verifies the user’s identity and, if successful, generates a security token or session cookie. This token is then used to provide access to the requested resource without requiring further authentication.
SSO implementations can vary, with different protocols and technologies employed, such as Security Assertion Markup Language (SAML), OpenID Connect, or OAuth. These protocols enable secure communication between the identity provider and the applications, ensuring the integrity and confidentiality of user authentication data.